How I learnt to generate custom word lists with Crunch
2016 May 22As I said on my first post, I'm taking a course on Ethical Hacking and in one of the exercises I had to exploit a Windows 7 machine. I learnt a lot trying to get into that system and one of those things was how to generate word lists using Crunch, here's the story.
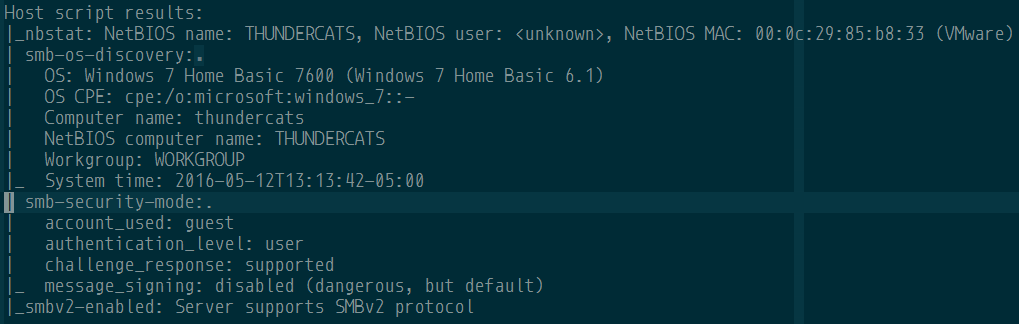
After a nmap scan, it showed that the machine had smb with user level authentication as you can see in the following image:
Given this, I thought about brute-forcing the password. To do this, I used the metasploit framework and the module auxiliary/scanner/smb/smb_login which basically attempts to log in with different passwords and determine if it can access the target.
One of the options of this module is PASS_FILE which is a path to a file with a list of passwords. On my first attempt, I used the password dictionary rockyou which is a huge dictionary that contains 14344392 passwords. After 30 minutes and hundreds of failed login attempts, I stopped the execution because it was going to take too much time and I wasn't very confident about it being successful, but I didn't give up on brute-forcing the password, I just thought that I needed a smaller dictionary.
Instead of using an existing dictionary I decided that I was going to create my own but where to start? After taking another look at the nmap scan results and seeing again that the machine name is "THUNDERCATS" I thought that maybe the password was related to that animated series. I also knew that the system language was Spanish so I went to the Wikipedia article about the Thundercarts in Spanish and I created a list with some keywords and the names of the main characters. This was going to be the base for my word list.
If you think about how people usually create their passwords, they normally put a word (a name, something they like, etc.) and add some numbers to it (a date, a "lucky" number, etc.). There are a lot more variables in a password, but to keep things simple I decided that I was going to generate my word list only with lowercase letters and a maximum of 4 numbers, so for instance if we have the word snarf, we'd have these password possibilities: snarf, snarf3, snarf05, snarf451, snarf9801, etc.
I already had my base words and the criteria I wanted to use, all I needed was a tool that helped me to generate the list. After googling a bit, I found crunch which its web page describes as:
"Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations."
After reading crunch's man page and some tutorials on the Internet I had some idea on how to use it, but I didn't find a way to generate the word list I wanted with a single command. Of course, I could generate it with multiple commands, but doing that manually was not an option. This was a good reason to learn a bit of bash and write my first script, this was the result:
#!/bin/bash
function generate_dictionary() {
patterns="$1 $1% $1%% $1%%% $1%%%%"
temp_path="/root/temp_dictionary.txt"
for pattern in $patterns;
do eval "crunch ${#pattern} ${#pattern} -t $pattern -o $temp_path";
cat $temp_path >> thundercats_dictionary.txt
done
rm $temp_path
}
words="thunder thundercats felino cosmico jaga leono leon-o tigro chitara panthro felina snarf thunderiano linxo linx-o pumara bengali mummra mumm-ra mutante reptilio mandrilok chacalom buitro mamutt ma-mutt lunatak amok alluro tugmug chilla ojorojo"
for word in $words;
do generate_dictionary $word
done
Finally, I was able to brute-force the password with a much smaller dictionary. Unfortunately, I wasn't able to get a correct username and password using this method :(, but hey! I've learnt a lot from this.
Cheers.